Code
This addon is free and open-source software (FOSS) all code can be found here: https://github.com/ACK-J/Port_Authority
Please report your bugs or feature requests in a GitHub issue instead of in a review.
Blog Post (Currently Down)
https://www.g666gle.me/Port-Authority/
Test if it works! (Currently Down)
https://www.g666gle.me/PortScan.html
What does this addon do?
- Blocks all possible types of port scanning (HTTP/HTTPS/WS/WSS/FTP/FTPS)
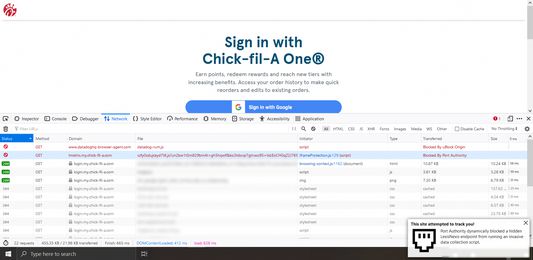
- Dynamically blocks the ThreatMetrix tracking scripts made by one of the largest and least ethical data brokers IMO (Lexis Nexis)
- Easily auditable, with the core functionality being about 250 lines of code. HERE
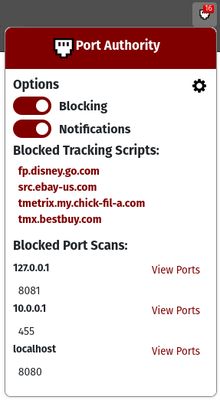
- Gives an optional notification when one of the above scenerios are blocked
- Provides an optional whitelist to prevent portscans and tracking scripts from being blocked on specified domains
- This addon doesn't store/transmit any data or metadata about you or your requests... because ya know privacy
If you are feeling generous or really like my work, consider donating
- Monero Address: 89jYJvX3CaFNv1T6mhg69wK5dMQJSF3aG2AYRNU1ZSo6WbccGtJN7TNMAf39vrmKNR6zXUKxJVABggR4a8cZDGST11Q4yS8
- Total donated (Aug 1, 2023): 0.0 XMR
Regex Explanation
- Explanation of the regex used to determine local addresses:
- https://regex101.com/r/DOPCdB/17
Explanation of the regex which is used to match the protocol: - https://regex101.com/r/f8LSTx/2
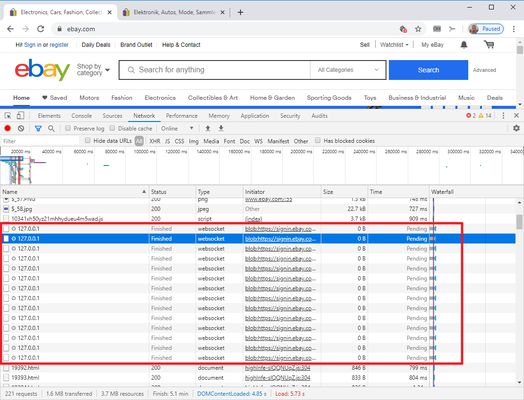
Test HTTP / HTTPS Portscanning
- Site where you can test if HTTP port scanning works: https://defuse.ca/in-browser-port-scanning.htm
- Site where you can test if HTTP port scanning works: https://inteltechniques.com/logger/
- Site where you can test if HTTP port scanning works (Output gives false positives): http://samy.pl/webscan/
- Click CTRL + Shift + I to see the networking tab where the blocked port scans will be shown.
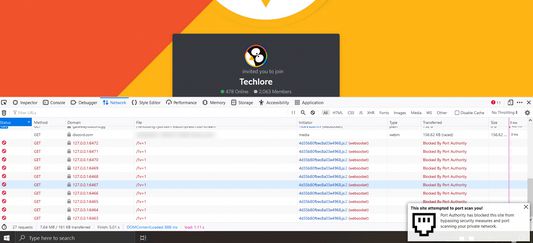
Test Websocket Portscanning
- Site where you can test if WebSocket port scanning works: https://discord.com/invite/32ZNZVN
- Blog Post
- Click CTRL + Shift + I to see the networking tab where the blocked port scans will be shown.
Sites that port scan you or otherwise run ThreatMetrix scripts (Wall of Shame) HERE
Permissions Needed
- Display notifications to you
- This is needed so the addon can alert you when a malicious scripts is blocked or javascrpt port scanning is blocked. Access browser tabs
- This is needed so the addon can display the proper number of blocked requests on a per-tab basis. Access your data for all websites
- This is needed because the addon needs to check every request your browser makes to determine if it needs to be blocked.
Warning!
- USING SOCKS5 PROXIES WITH THIS ADDON WILL CAUSE DNS LEAKS DUE TO HOW FIREFOX HANDLES CNAME LOOKUPS. FOR MORE INFORMATION SEE HERE https://github.com/ACK-J/Port_Authority/issues/7#issue-925519591
- There is a simple fix for this. Type about:config in your browser, accept the warning, search for network.trr.mode and change it to 3
Why I wrote this addon?
Back in May of 2020 eBay got caught port scanning their customers. I noticed that all of the articles covering this topic mentioned that there was nothing you could do to prevent it... so I wanted to make one. After going down many rabbit holes, I found that this script which was port scanning everyone is, in my opinion, malware.
Here's why I think that:
- The data being exfiled from your computer is encrypted into an image using XOR.
- The domain it reaches out to is made to look legitimate but redirects using a CNAME record to Lexis Nexis' servers.
- It can determine your real IP address even if you are using a VPN / Proxy HERE. This is likely due to the aggressive fingerprinting.
- The JavaScript is assembled via string.join (like malware often does) and then executed in a service worker.
- Each time you load the page the JavaScript is re-obfuscated. This makes debugging what they are doing extremely difficult.
- The script collects 416 pieces of personally identifiable information about you and your network. ( Shown HERE )
Note: This second method will never include every customer-specific endpoint so you are better off using the dynamic blocking built into Port Authority which WILL block every single customer-specific endpoint Lexis Nexis uses.
Most of these sites are using Lexis Nexis's Threat Metrix scripts, Dan Nemec has a great blog post reverse engineering the script and showing all the invasive data collected https://blog.nem.ec/2020/05/24/ebay-port-scanning/
 Install
Install
- License: GNU General Public License v2.0 or later
- Weekly downloads: 55
- Average daily users: 1081
- Rating: 4.7143/5 of 14 ratings
- Created: 2021-03-22 02:26:15
- Last updated: 2023-08-03 11:45:24
- Homepage: https://github.com/ACK-J/Port_Authoirty
- Support site and email
- Orig: https://addons.mozilla.org/en-US/firefox/addon/port-authority/
- API: {6c00218c-707a-4977-84cf-36df1cef310f}